For the first time, researchers have mapped all the known targets, including journalists, activists, and human rights defenders, whose phones were hacked by Pegasus, a spyware developed by NSO Group.
Forensic Architecture, an academic unit at Goldsmiths, University of London that investigates human rights abuses, scoured dozens of reports from human rights groups, carried out open-source research and interviewed dozens of the victims themselves to reveal over a thousand data points, including device infections, which show relations and patterns between digital surveillance carried out by NSO’s government customers, and the real-world intimidation, harassment and violence that the victims are also subject to.
By mapping out these data points on a bespoke platform, the researchers can show how nation-states, which use Pegasus to spy on their victims, also often target other victims in their networks and are entangled with assaults, arrests, and disinformation campaigns against the targets but also their families, friends, and colleagues.
Although the thousand-plus data points only present a portion of the overall use of Pegasus by governments, the project aims to provide researchers and investigators the tools and data of NSO’s activities worldwide, which the spyware maker goes to great lengths to keep out of the public eye.
Pegasus “activates your camera, your microphone, all that which forms an integral part of your life.” Mexican journalist Carmen Aristegui
Israel-based NSO Group develops Pegasus, a spyware that allows its government customers near-unfettered access to a victim’s device, including their personal data and their location. NSO has repeatedly declined to name its customers but reportedly has government contracts in at least 45 countries, said to include Rwanda, Israel, Bahrain, Saudi Arabia, Mexico, and the United Arab Emirates — all of which have been accused of human rights abuses — as well as Western nations, like Spain.
Forensic Architecture’s researcher-in-charge Shourideh Molavi said the new findings reveal “the extent to which the digital domain we inhabit has become the new frontier of human rights violations, a site of state surveillance and intimidation that enables physical violations in real space.”
The platform presents visual timelines of how victims are targeted by both spyware and physical violence as part of government campaigns to target their most outspoken critics.
Omar Abdulaziz, a Saudi video blogger and activist living in exile in Montreal, had his phone hacked in 2018 by the Pegasus malware. Shortly after Saudi emissaries tried to convince Abdulaziz to return to the kingdom, his phone was hacked. Weeks later, two of his brothers in Saudi Arabia were arrested and his friends detained.
Abdulaziz, a confidant of Washington Post journalist Jamal Khashoggi whose murder was approved by Saudi’s de facto ruler Crown Prince Mohammed bin Salman, also had information about his Twitter account obtained by a “state-sponsored” actor, which later transpired to be a Saudi spy employed by Twitter. It was this stolen data, which included Abdulaziz’s phone number, that helped the Saudis penetrate his phone and read his messages with Khashoggi in real-time, Yahoo News reported this week.
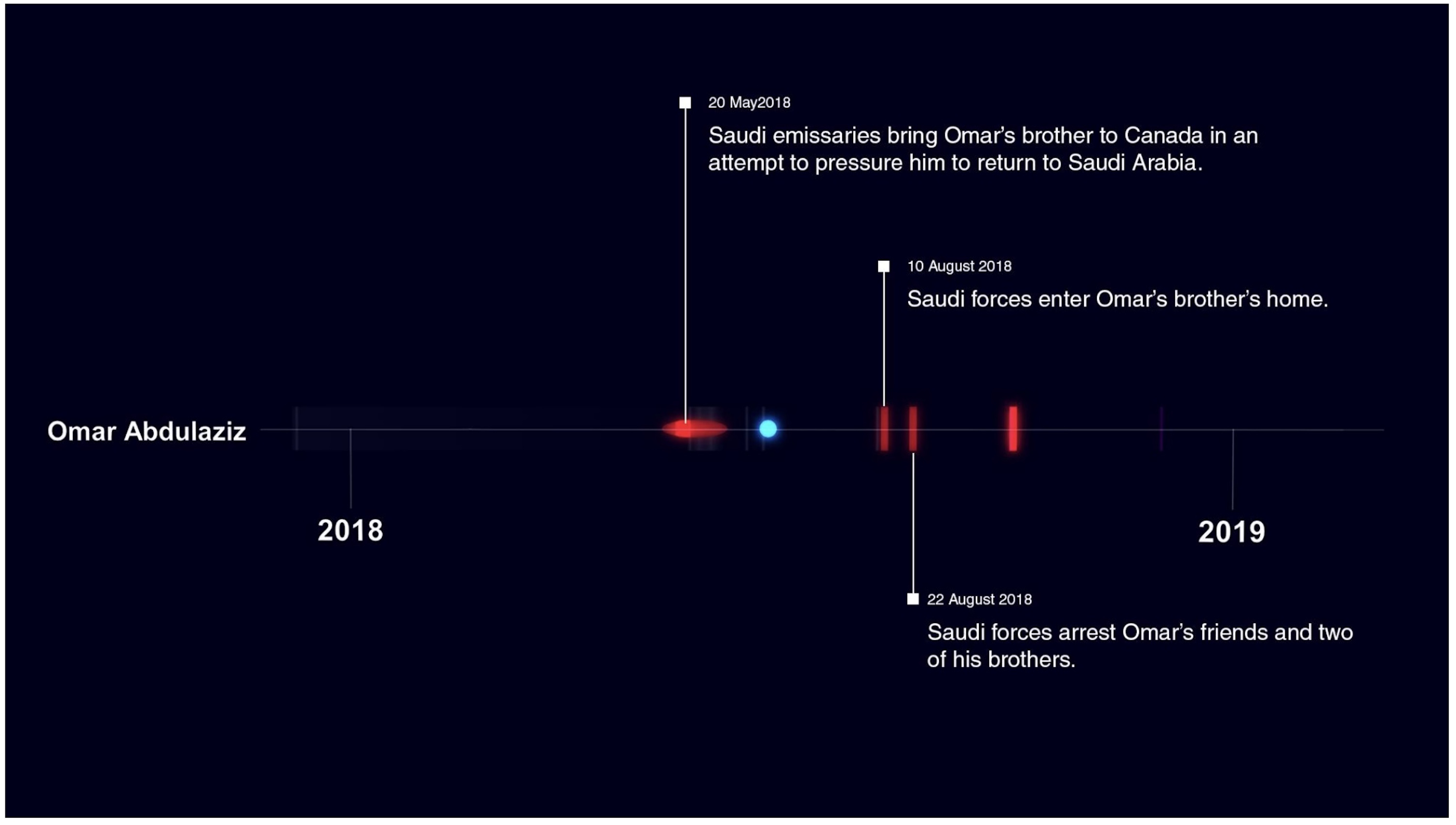
Omar Abdulaziz is one of dozens of known victims of digital surveillance by a nation state. Blue dots represent digital intrusions and red dots indicate physical events, such as harassment or violence. (Image: Forensic Architecture/supplied)
Mexican journalist Carmen Aristegui is another known victim, whose phone was hacked several times over 2015 and 2016 by a government customer of Pegasus, likely Mexico. The University of Toronto’s Citizen Lab found that her son, Emilio, a minor at the time, also had his phone targeted while he lived in the United States. The timeline of the digital intrusions against Aristegui, her son, and her colleagues show that the hacking efforts intensified following their exposure of corruption by Mexico’s then-president Enrique Peña Nieto.
“It’s a malware that activates your camera, your microphone, all that which forms an integral part of your life,” said Aristegui in an interview with journalist and filmmaker Laura Poitras, who contributed to the project. Speaking of her son whose phone was targeted, Aristegui said: “To know that a kid who is simply going about his life, and going to school tells us about the kinds of abuse that a state can exert without counterweight.” (NSO has repeatedly claimed it does not target phones in the United States, but offers a similar technology to Pegasus, dubbed Phantom, through U.S.-based subsidiary, Westbridge Technologies.)
“A phenomenal damage is caused to the journalistic responsibility when the state — or whoever — uses these systems of ‘digital violence’,” said Aristegui. “It ends up being a very damaging element for journalists, which affects the right of a society to keep itself informed.”
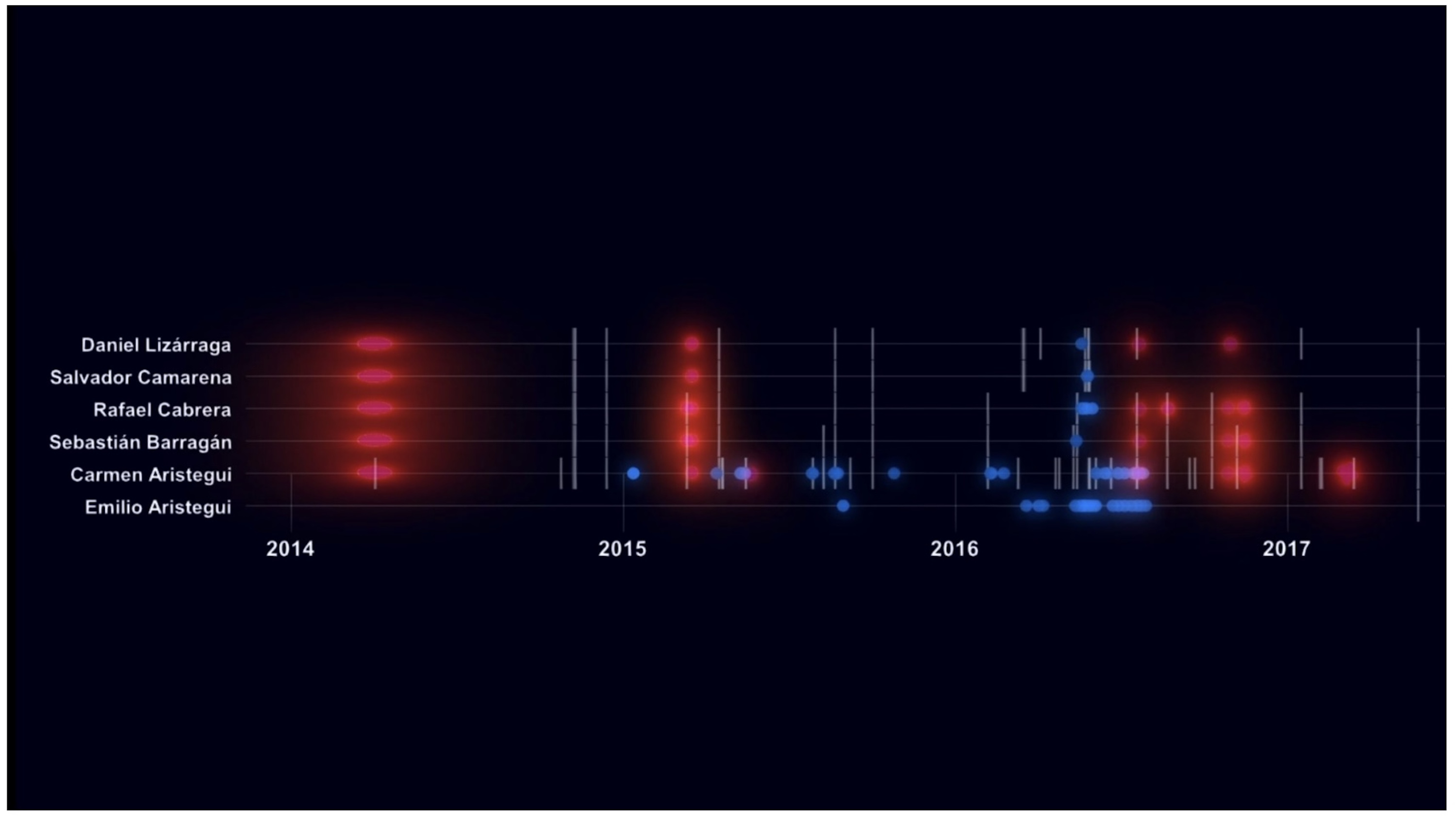
The timeline also shows the digital targeting (in blue) of Carmen Aristegui, her family, and her colleagues, entangled with break-ins at their office, intimidation, and disinformation campaigns (in red). (Image: Forensic Architecture/supplied)
The platform also draws on recent findings from an Amnesty International investigation into NSO Group’s corporate structure, which shows how NSO’s spyware has proliferated to states and governments using a complex network of companies to hide its customers and activities. Forensic Architecture’s platform follows the trail of private investment since NSO’s founding in 2015, which “likely enabled” the sale of the spyware to governments that NSO would not ordinarily have access to because of Israeli export restrictions.
“NSO Group’s Pegasus spyware needs to be thought of and treated as a weapon developed, like other products of Israel’s military industrial complex, in the context of the ongoing Israeli occupation. It is disheartening to see it exported to enable human rights violations worldwide,” said Eyal Weizman, director of Forensic Architecture.
The platform launched shortly after NSO published its first so-called transparency report this week, which human rights defenders and security researchers panned as devoid of any meaningful detail. Amnesty International said the report reads “more like a sales brochure.”
In a statement, NSO Group said it cannot comment on research it has not seen, but claimed it “investigates all credible claims of misuse, and NSO takes appropriate action based on the results of its investigations.”
NSO Group maintained that its technology “cannot be used to conduct cybersurveillance within the United States, and no customer has ever been granted technology that would enable them to access phones with U.S. numbers,” and declined to name any of its government customers.
You can send tips securely over Signal and WhatsApp to +1 646-755-8849. You can also send files or documents using our SecureDrop. Learn more.
from TechCrunch https://ift.tt/3qJstfq



No comments:
Post a Comment