Since the start of the outbreak, governments and companies have scrambled to develop apps and websites that can help users identify COVID-19 symptoms.
India’s largest cell network Jio, a subsidiary of Reliance, launched its coronavirus self-test symptom checker in late March, just before the Indian government imposed a strict nationwide lockdown to prevent the further spread of the coronavirus. The symptom checker allows anyone to check their symptoms from their phone or Jio’s website to see if they may have become infected with COVID-19.
But a security lapse exposed one of the symptom checker’s core databases to the internet without a password, TechCrunch has found.

Jio’s coronavirus symptom checker. One of its databases exposed users’ responses. (Image: TechCrunch)
Security researcher Anurag Sen found the database on May 1, just after it was first exposed, and informed TechCrunch to notify the company. Jio quickly pulled the system offline after TechCrunch made contact. It’s not known if anyone else accessed the database.
“We have taken immediate action,” said Jio spokesperson Tushar Pania. “The logging server was for monitoring performance of our website, intended for the limited purpose of people doing a self-check to see if they have any COVID-19 symptoms.”
The database contains millions of logs and records starting April 17 through to the time that the database was pulled offline. Although the server contained a running log of website errors and other system messages, it also ingested vast numbers of user-generated self-test data. Each self-test was logged in the database and included a record of who took the test — such as “self” or a relative, their age, and their gender.
The data also included the person’s user agent, a small snippet of information about the user’s browser version and the operating system, often used to load the website properly but can also be used to track a user’s online activity.
The database also contains individual records of those who signed up to create a profile, allowing users to update their symptoms over time. These records contained the answers to each question asked by the symptom checker, including what symptoms they are experiencing, who they have been in contact with, and what health conditions they may have.
Some of the records also contained the user’s precise location, but only if the user allowed the symptom checker access to their browser or phone’s location data.
We’ve posted a redacted portion of one of the records below.
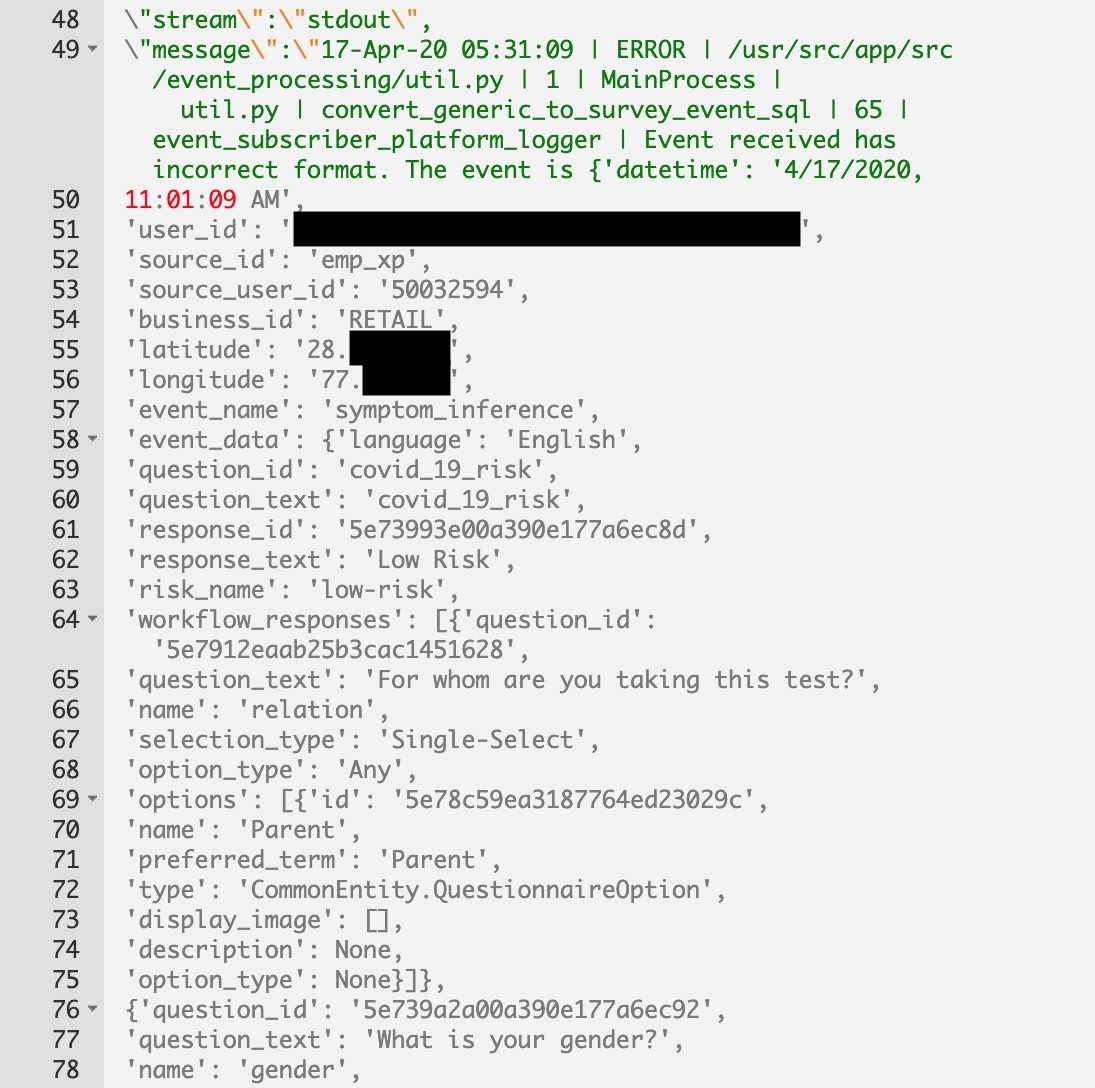
A redacted portion of the exposed database. (Image: TechCrunch)
From one sample of data we obtained, we found thousands of users’ precise geolocation from across India. TechCrunch was able to identify people’s homes using the latitude and longitude records found in the database.
Most of the location data is clustered around major cities, like Mumbai and Pune. TechCrunch also found users in the United Kingdom and North America.
The exposure could not come at a more critical time for the Indian telecoms giant. Last week Facebook invested $5.7 billion for a near-10% stake in Jio’s Platforms, valuing the Reliance subsidiary at about $66 billion.
Jio did not answer our follow-up questions, and the company did not say if it will inform those who used the symptom tracker of the security lapse.
from TechCrunch https://ift.tt/2VXJ81h



No comments:
Post a Comment